Windows Server Brute Force Protection
Applicable to:
- Windows Server 2019 / 2022
Disable brute force protection
Microsoft has implemented a feature named, “Account lockout for built-into local administrator”, as part of update KB5020282, which locks out the Administrator account after 10 failed password attempts within 10 minutes.
As Self-Managed Servers are provisioned with static IP ranges, it’s common to encounter brute force attacks that may lead to the Administrator account being locked out.
You can change the settings for this security policy, or turn it off entirely in the “Local Security Policy”. This can be found in the “Server Manager”, by clicking on “Tools” and “Local Security Policy”.
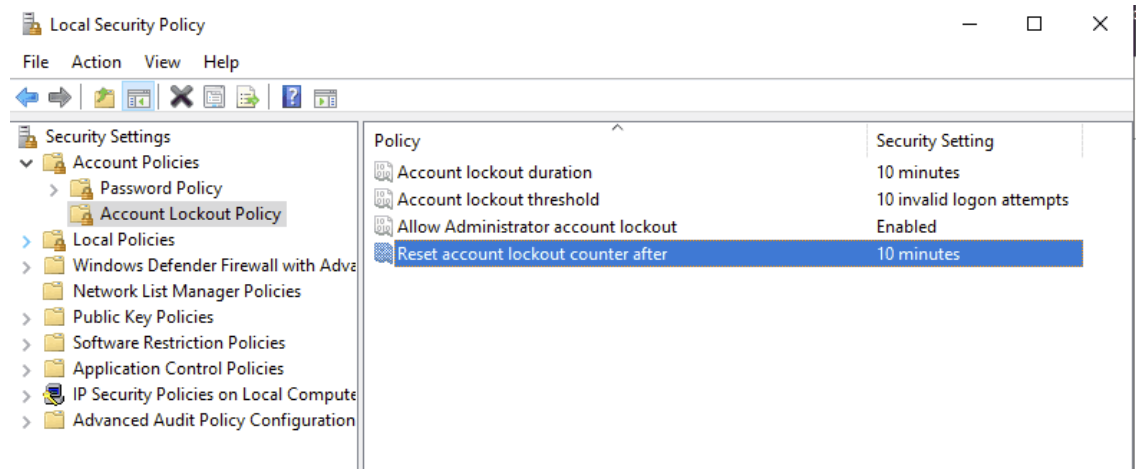
This feature is disabled by default for new installations.