Self-Managed Server Remote Management security
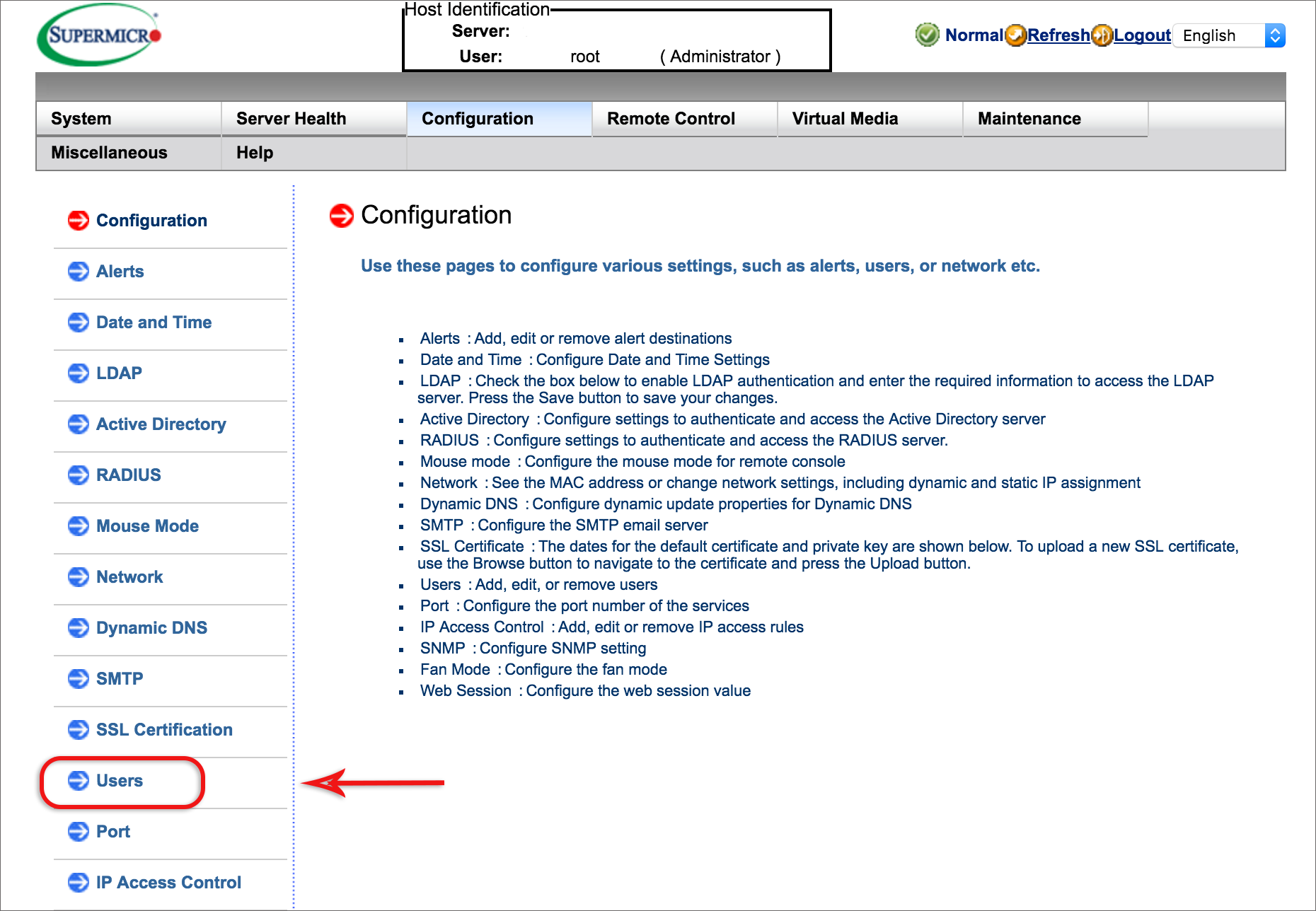
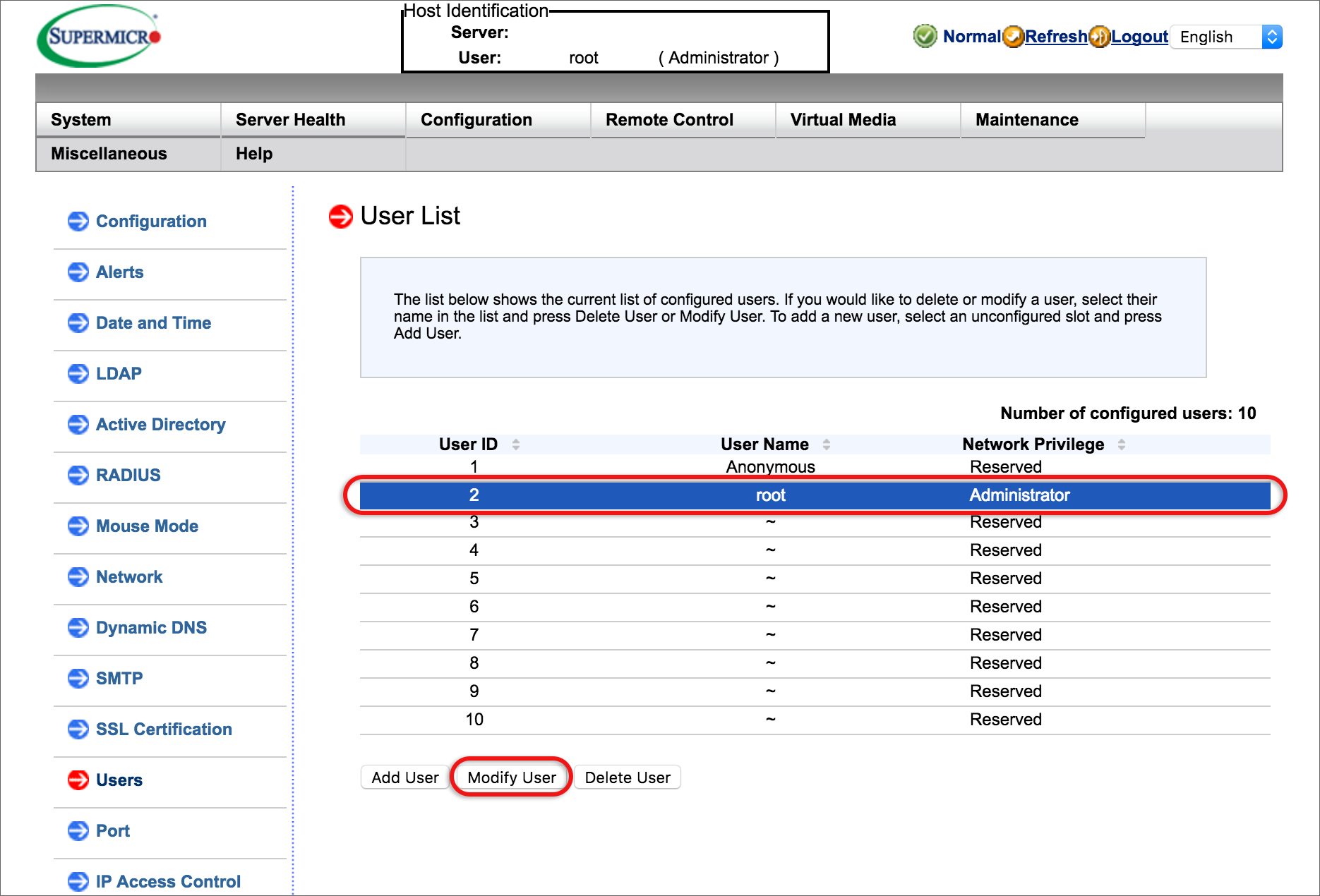
What is the RMI or Remote Control?
The Remote Management Interface or Remote Control is a remote access and management hardware module that allows you to set up and troubleshoot your Self-Managed Server from a remote location. This feature, included with all Self-Managed products, can be used for:
- Initial server setup and troubleshooting
- Server recovery and maintenance
- Remote access to allow complete power control and software installation maintenance
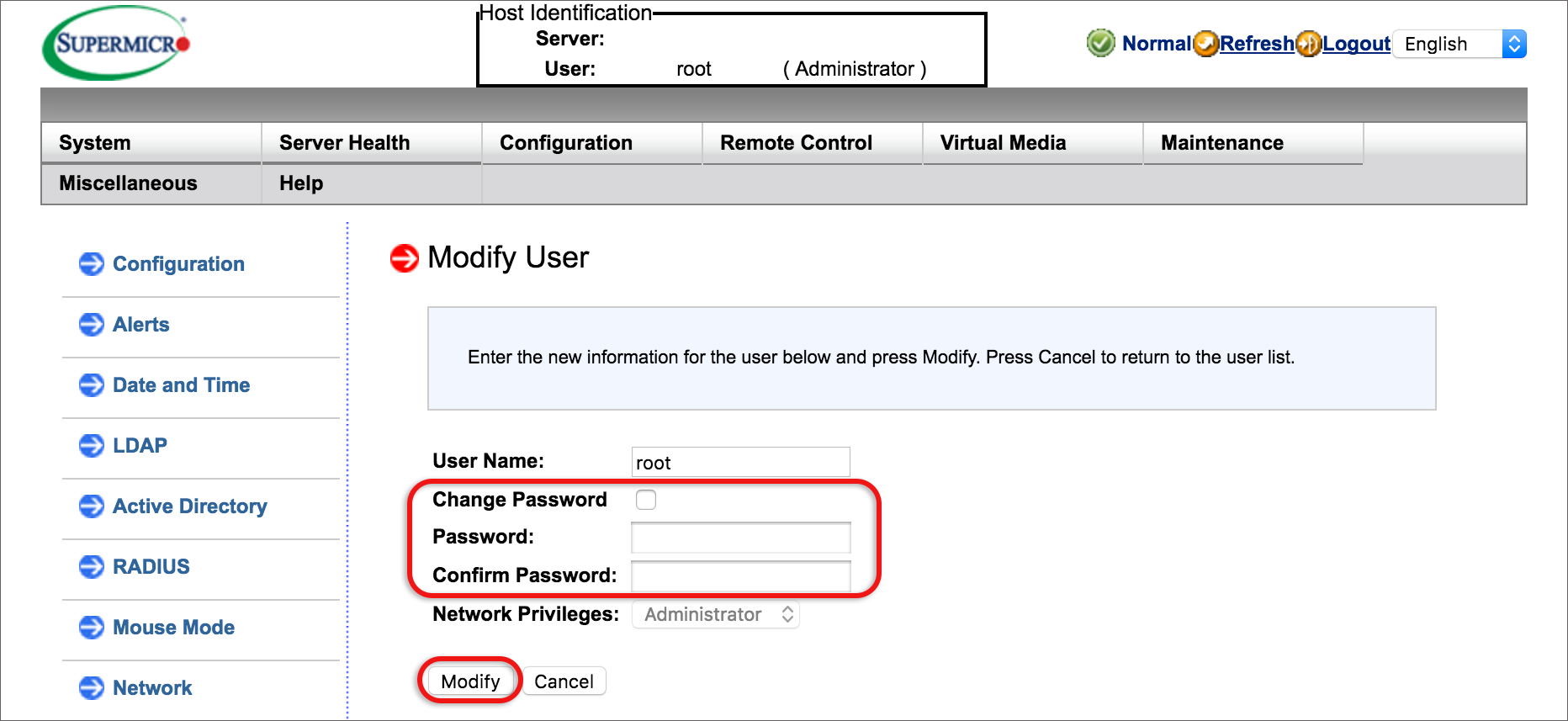
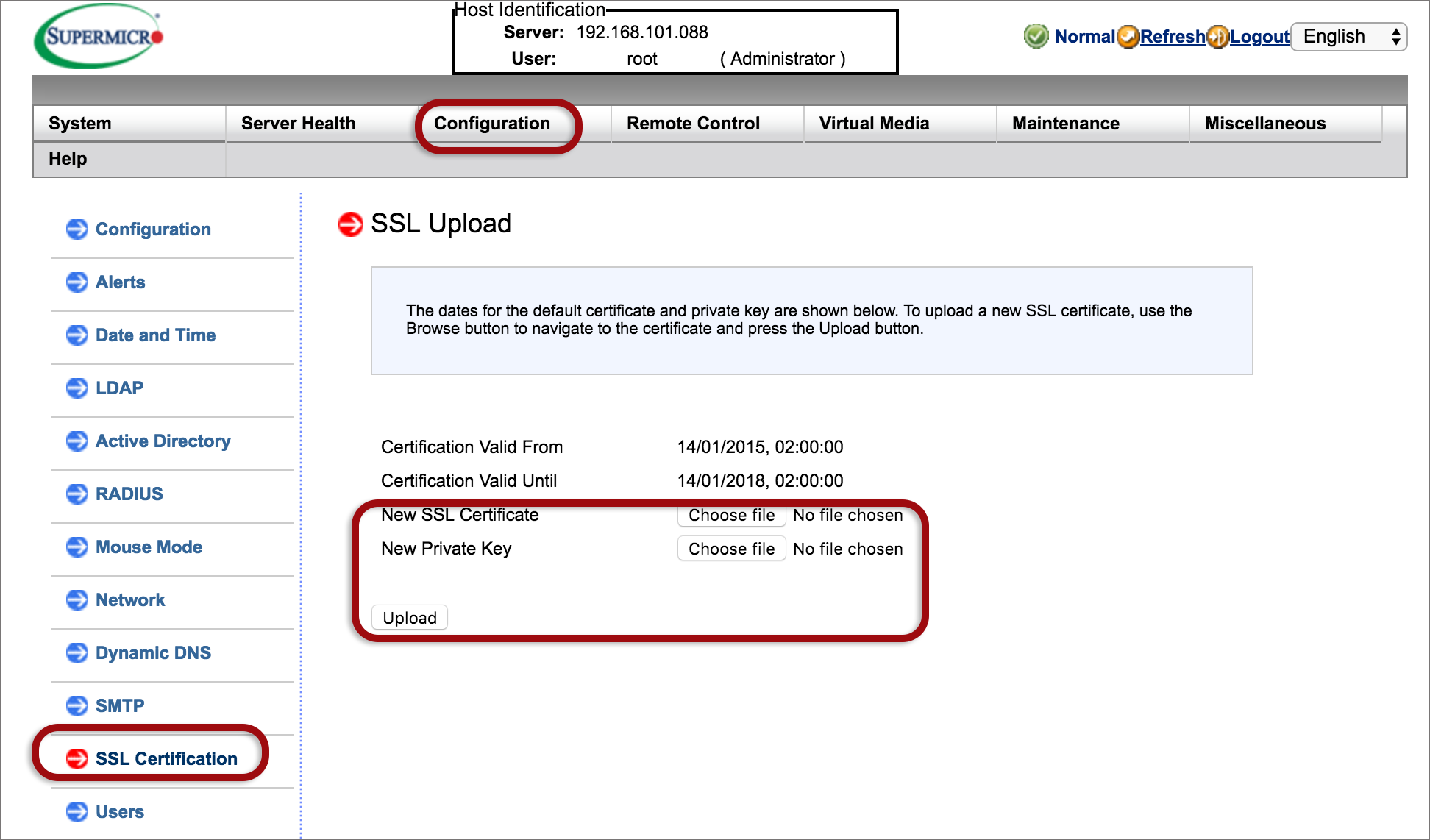
Important Security recommendations
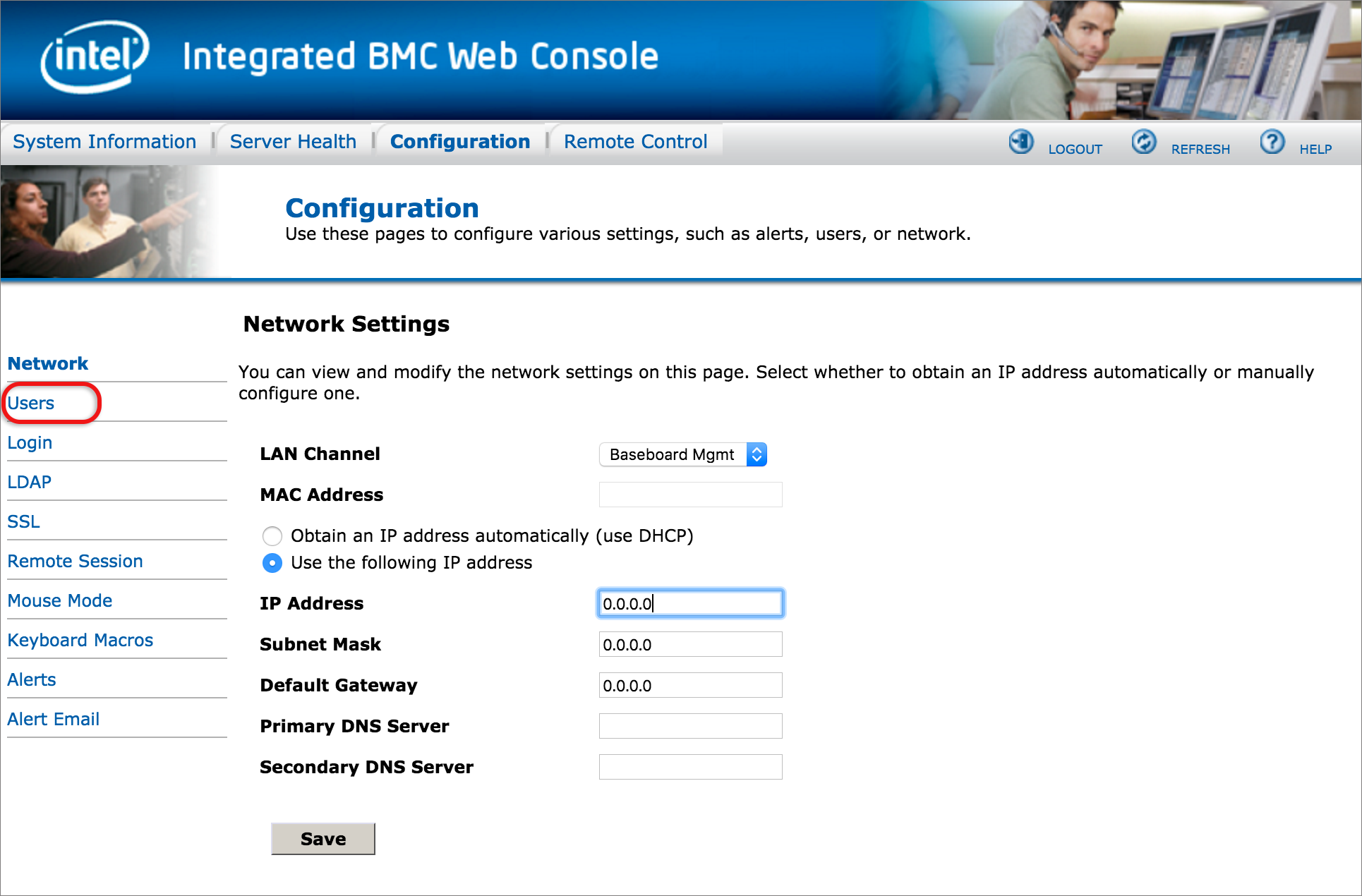
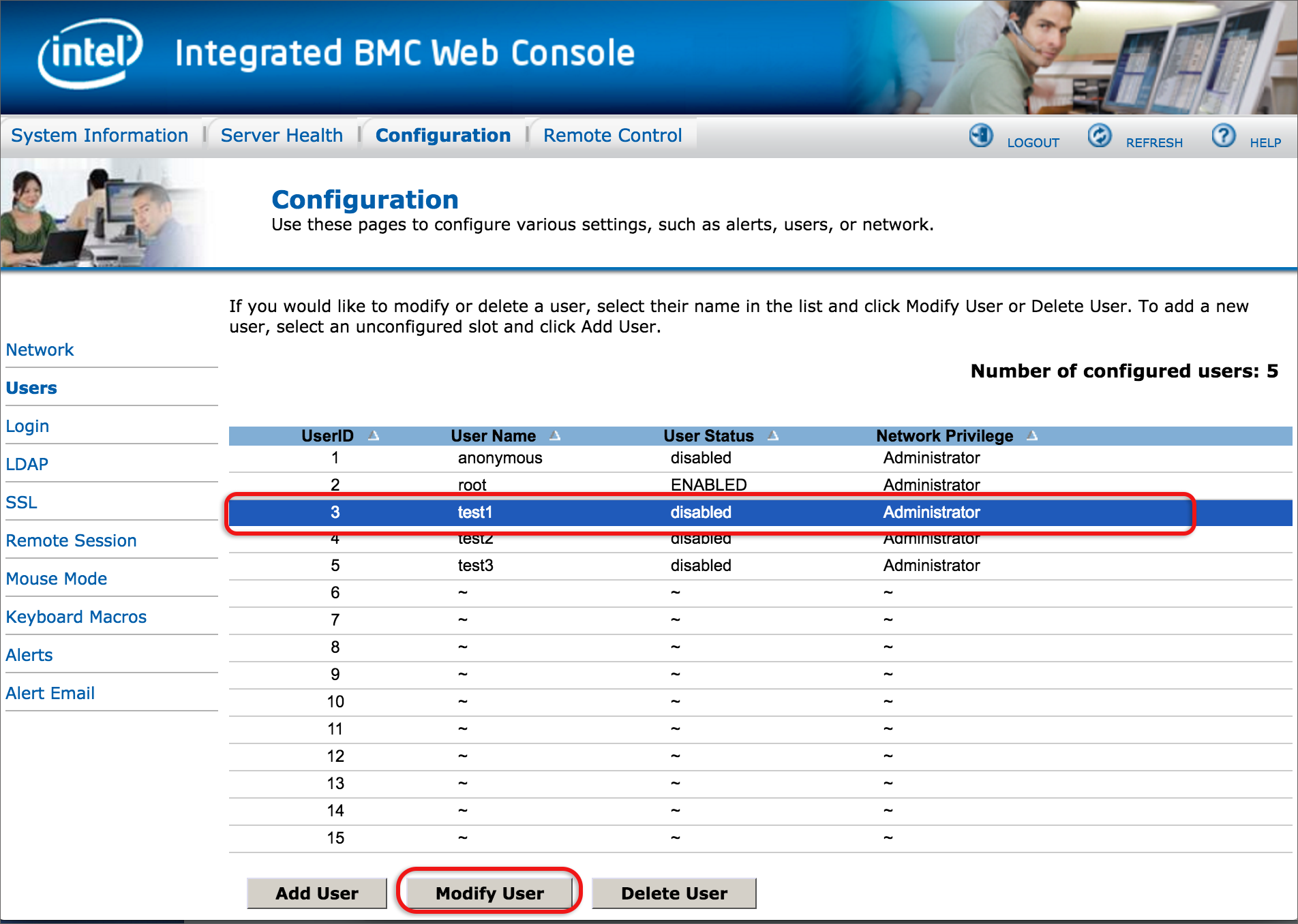
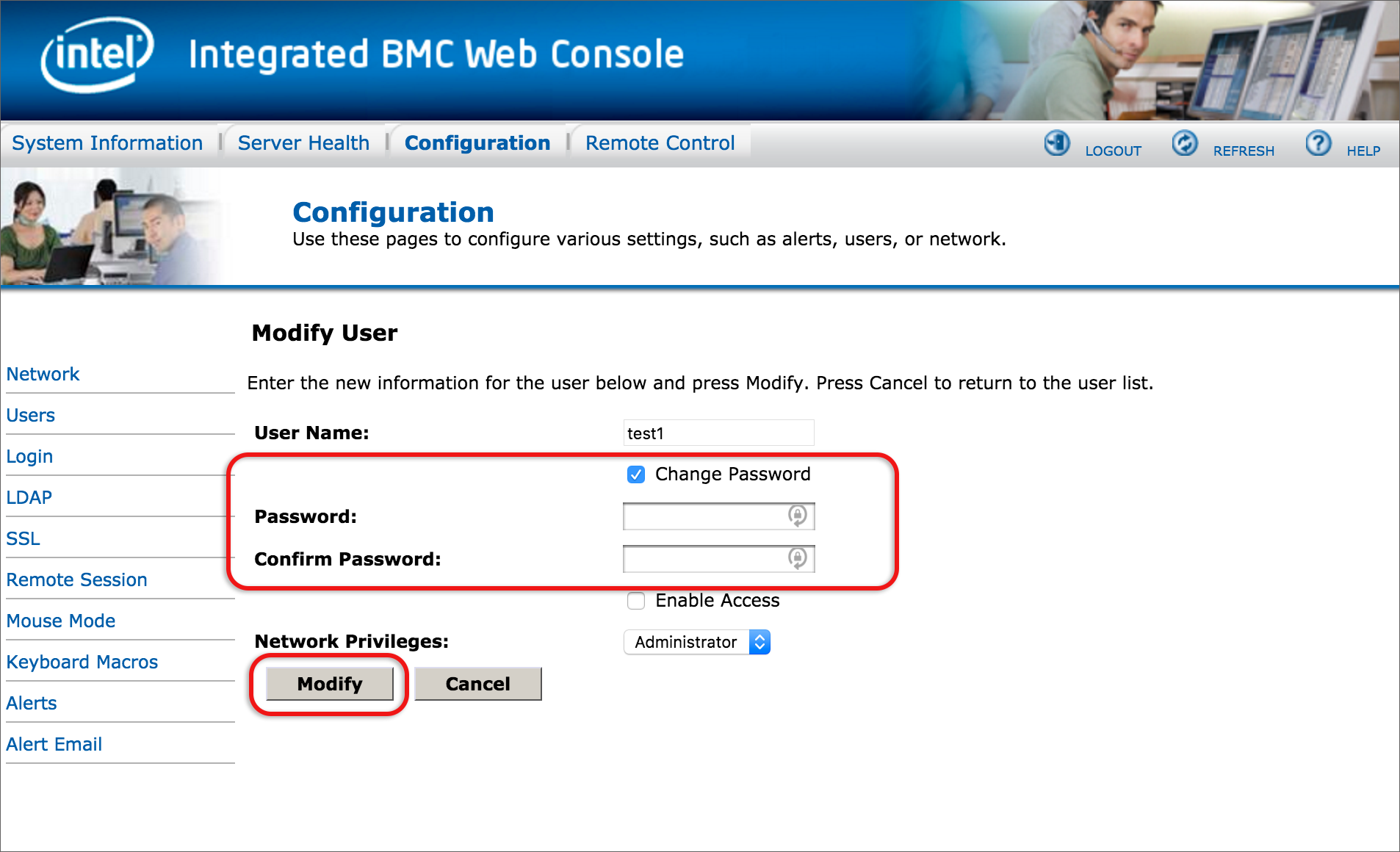
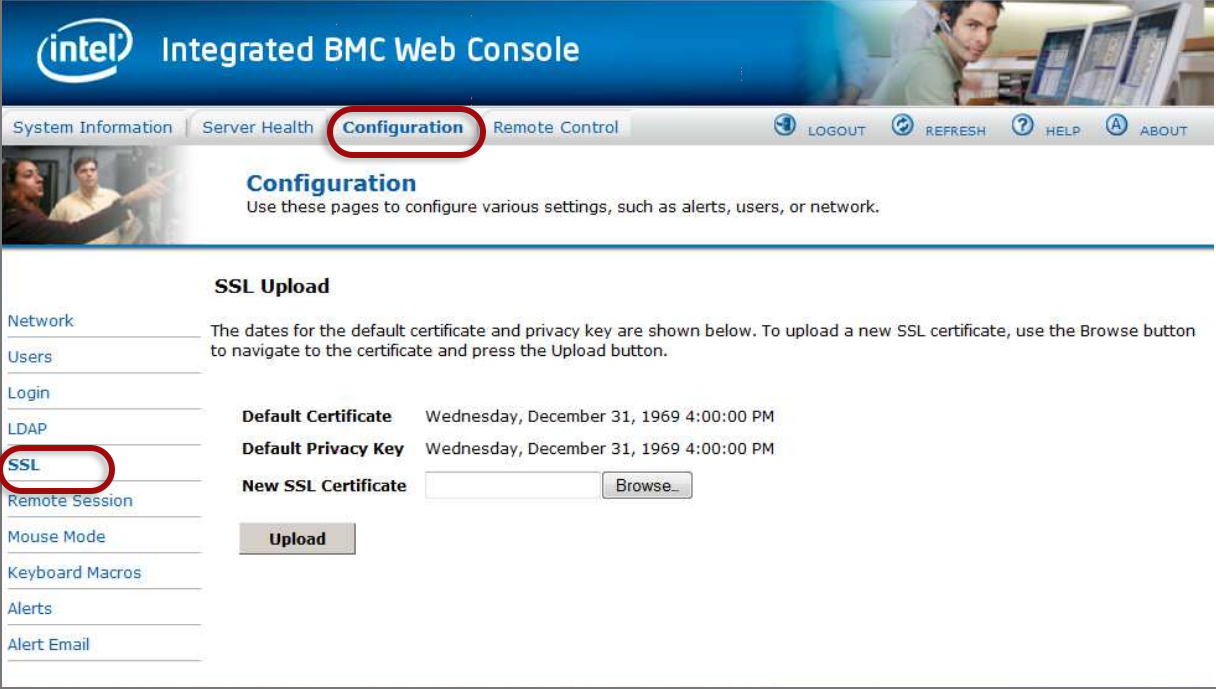
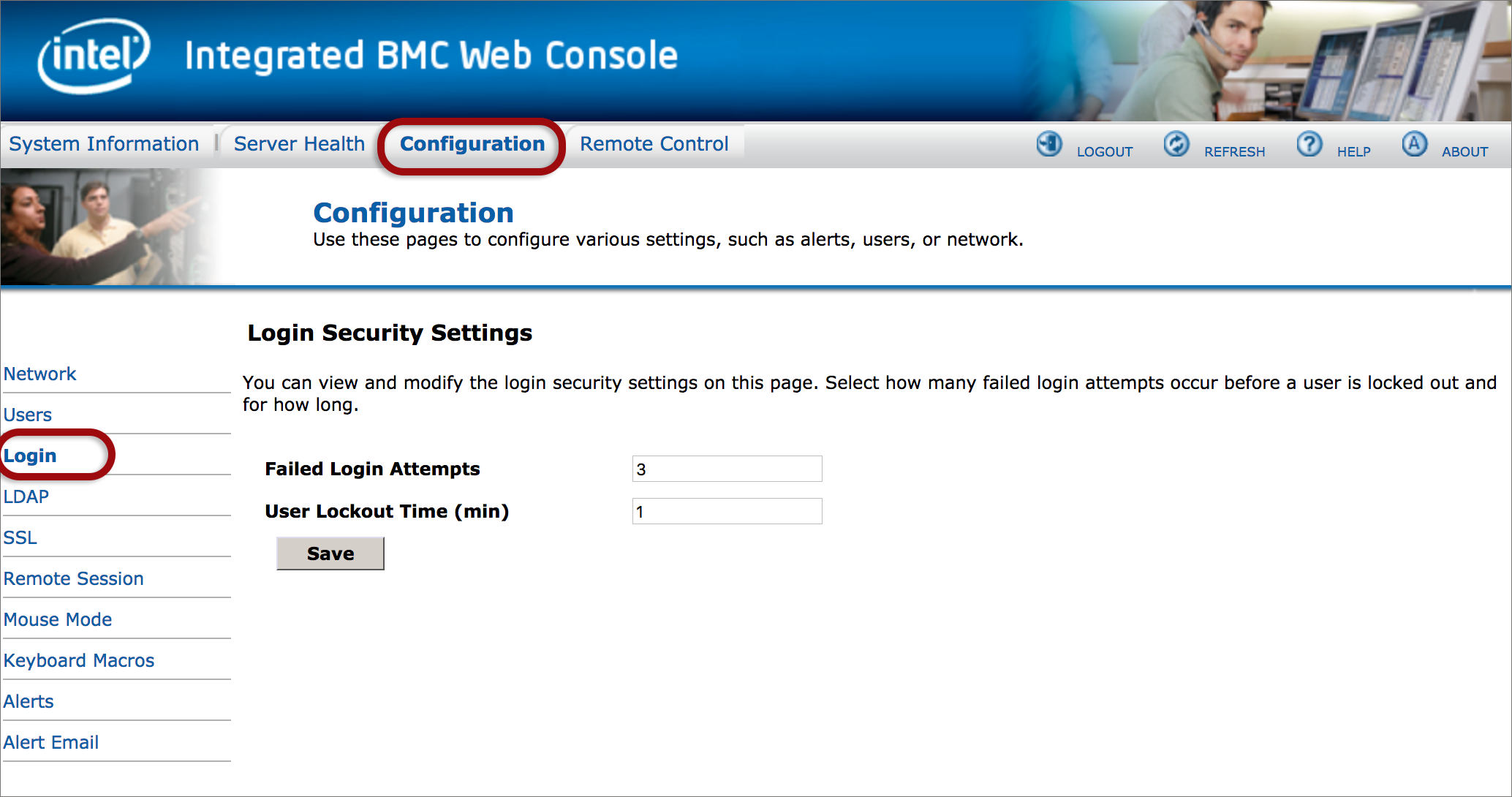
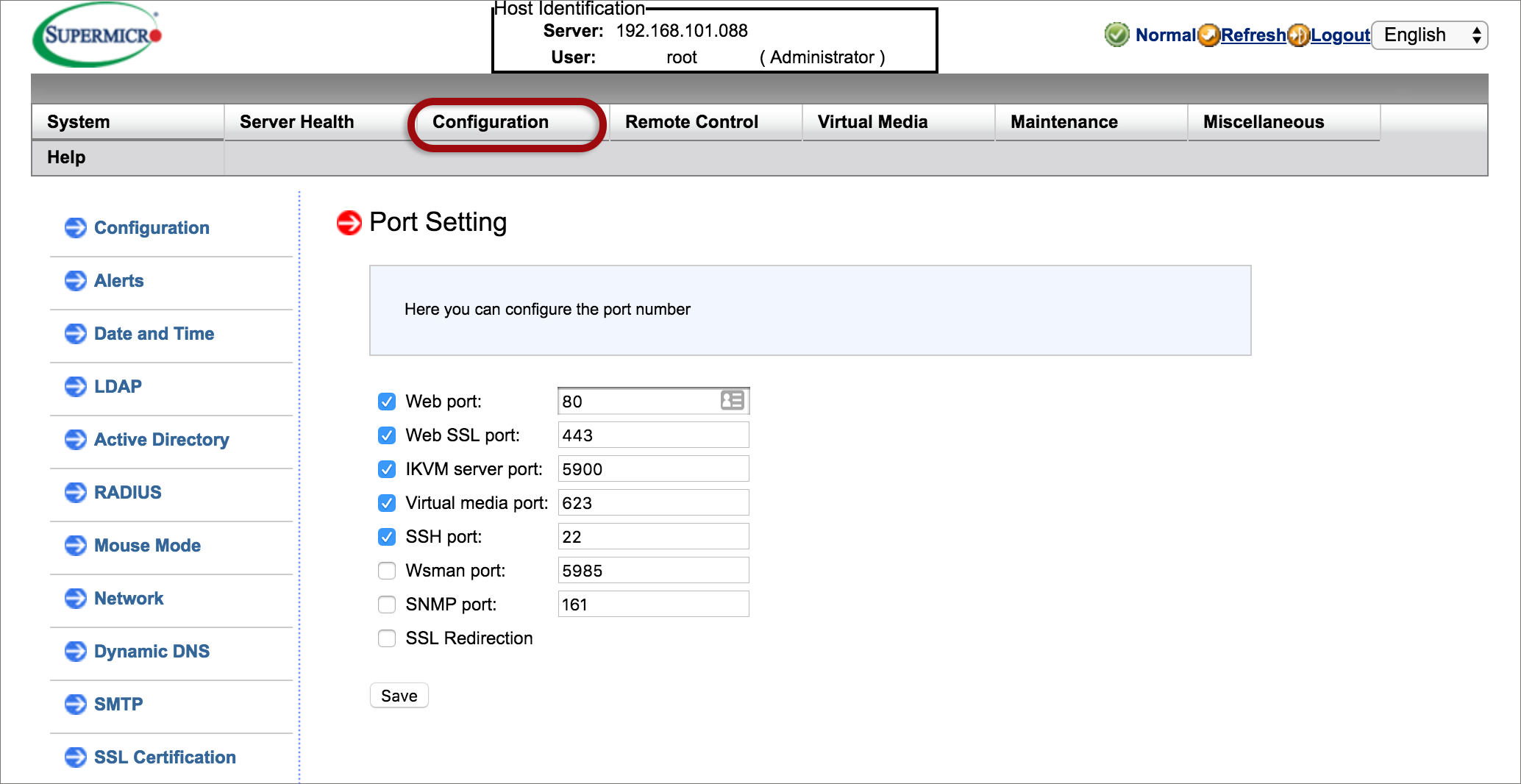
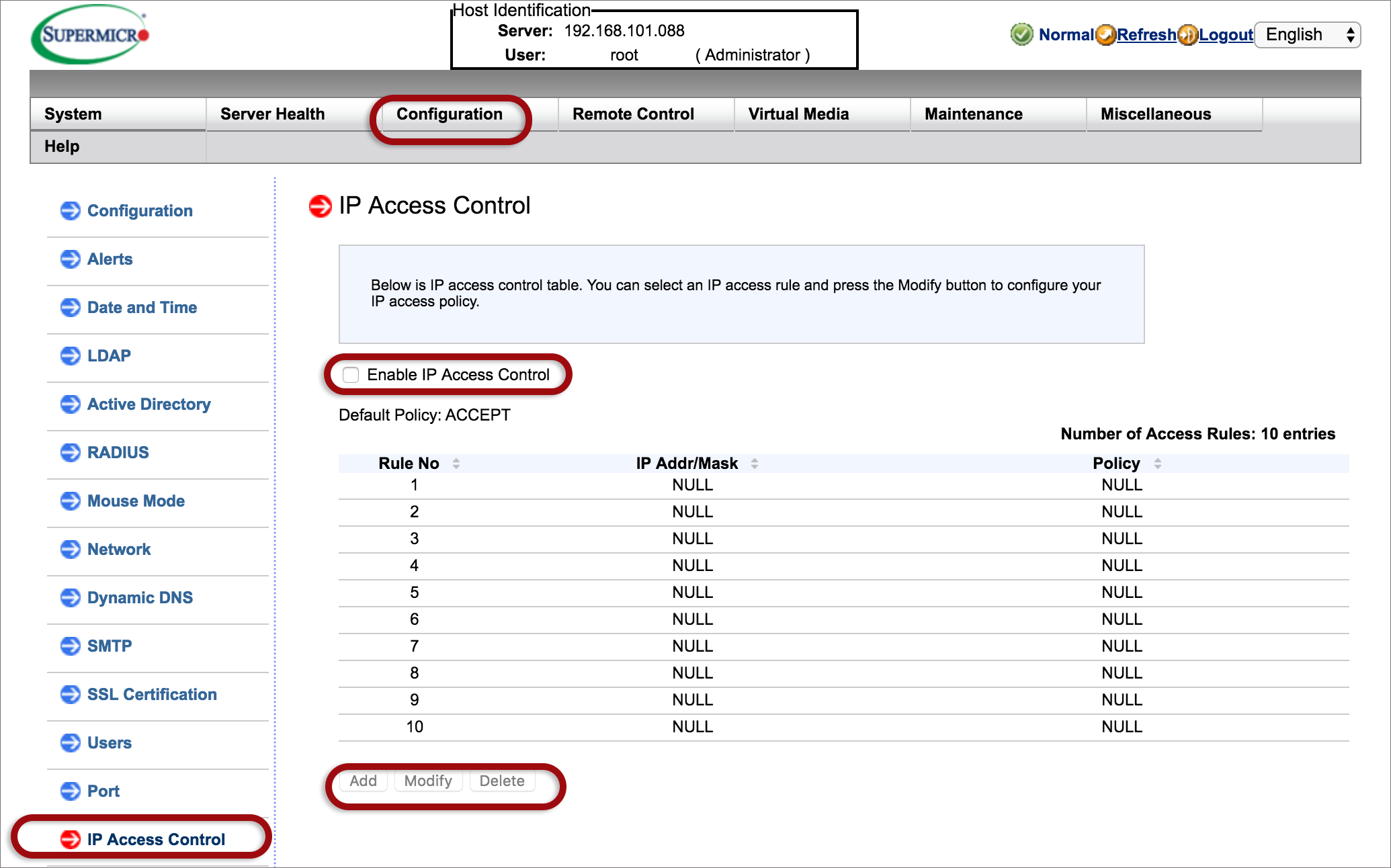
If you’re using a public IP address to access the RMI, please implement these security measures to prevent this device and IP from being used in abuse scenarios (eg: external attacks of 3rd party systems or sending spam mails via the mail sending mechanism).
The following security measures are recommended according to your relevant software:

All Self-Managed tools and features are now available in the new xneelo Control Panel. Make the switch to the new xneelo Control Panel and discover a simpler, more secure way to manage your hosting.